Threat
Calvin (Deutschbein)
11 January 2023
Announcements
- Welcome to DATA-599: Cybersecurity!
- Things to do:
- Access the course webpage at cd-public.github.io/courses/sec
- There will be a link to the course webpage from the WISE site
- Look over the syllabus
- Join the Discord!
- You should have gotten an email
- Access the course webpage at cd-public.github.io/courses/sec
- Homework
- The first homework, "Threat Modeling" will be presented at the beginning of next class, due next Wednesday, 1/18
About Me
- Name
- Calvin (Deutschbein)
- Pronouns
- they/them
- Office
- Ford 206 (in SALEM 💀)
- Office Hours
- Zoom by appt (email or discord me)
- Tuesdays and Thursdays are better.
- Email:
- ckdeutschbein@willamette.edu
- Website:
- cd-public.github.io
Background
- Thesis Title
- Mining Secure Behavior of Hardware Designs
- Plain English
- Just as there are bugs in code that makes software, modern hardware is also written in code and therefore may contain bugs. I find these bugs.
- Thesis
- Specification mining can discover properties that can be used to verify the secure behavior of closed source CISC CPU designs, properties that can be used to verify the temporal correctness of CPU designs, and hyperproperties that can be used to verify that modules, SoCs, and CPUs have secure information flow.
- Some partners
- Intel Corporation, Semiconductor Research Corporation, Synopsys, MITRE, Cycuity
Motivations
- Computers are just like everything else. But it can be hard to remember this!
- When reasonable precautions are not taken, problems arise affecting security and privacy.
- Studying cybersecurity now lets you take part in driving forward not only the fields of data and computing, but of all the modern fields with utilize technology.
- Almost all fields!
Learning Objectives
To gain the skills, knowledge, and confidence necessary to for reasoning about information and computing and controlled accesses to these resources.
Doing so will require that students be able to:
- practice styles of thinking common to security researchers,
- exploring some coding styles for secure development,
- gain historical context of the importance of security,
- learn the logical foundations of security,
- experience state-of-the-art security research
Tests
- Tests are a useful tool to promote directed thinking about the science of computing in isoloation from a programming environment.
- Just two this semester:
- Midterm I on 2/22
- Midterm II on 4/12
- Having two tests reduces the stakes of the individual test and hopefully reduces stress as well!
- Tests will be taken in class*.
- This policy has actually been seen to improve student learning, as it prevents you from wasting tons of time obsessing about a small mistake!
- Example tests and study materials will be given out a week in advance.
Communication
- I tend to find WISE lacking both from a polish perspective and from an ease of use perspective
- I will be using a 3rd-party forum to focus class communication, announcements, and questions: Discord.
- You should have gotten an email with invite instructions. Let me know if you have not!
- Totally free to sign up and use
Diving In
- This course is an introduction on security, and covers more than just programming!
- Programming will be used to teach the computing portion of the course, but the focus is less on programming itself and more on general computer ssecurity principles.
- If you come across situations where you need to know a bit more about specific programming details, there are plenty of resources online, or just ask me!
Threat
- What is secure?
- For whom is the 'what' secure?
- From whom is the 'what' secure?
"Security" is incomplete as a concept.
Brainstorming
- What are some things that we think of as being secure?
- What computer systems?
- What non-computing things?
- Is there a boundary between these?
- What does "security" mean to you?
- What about "secure" as an adjective?
- What about "secure" as a verb?
- Form groups of 2-4 and create a definiton of "secure" and "security". [5-10 min]

Messaging
Consider and end-to-end messaging service.
- Messaging is secure.
- For all senders and receivers the messaging is secured.
- From any third party the messaging service is secured.
Limitations
What does this leave out?
- Can a third party tell who uses the service?
- Can a third party tell when messages are being sent?
- Can a third party tell the length of the messages?
Do these matter?
Who decides?
Clarity Matters
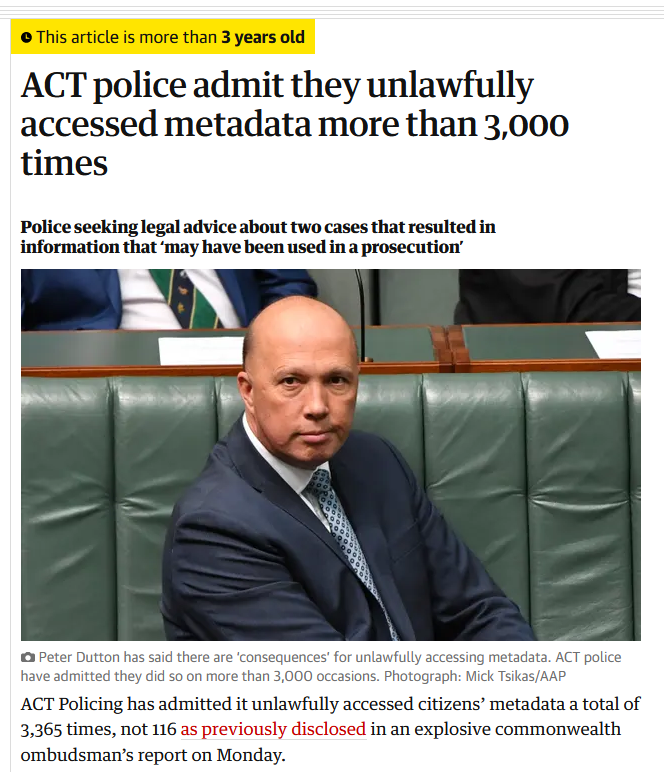
- In 2019, Federal Police in Australia were taken to court.
- They illegally accessed "metadata".
- When caught, they lied about whether they did it or not.
- When caught again, they lied about how many times they did it.
- We still don't know if we know the extent of illegal access.
- Form groups of 2-4 and discuss: How can we address this environment as scientists of data and computing? [5 min]
Threat Modeling
A more complete solution to security analysis is threat modeling.
A threat model typically addresses:
- Description of the subject to be modeled
- Assumptions that can be checked or challenged in the future as the threat landscape changes
- Potential threats to the system
- Actions that can be taken to mitigate each threat
- A way of validating the model and threats, and verification of success of actions taken
Read more: OWASP.org
Looping back!
This is what we have been doing!
| Informally | Formally |
|---|---|
| What? | Description of the subject to be modeled |
| For whom? | A way of validating the model and threats, and verification of success of actions taken |
| From whom? | Potential threats to the system |
| Any limitations? | Assumptions that can be checked or challenged in the future as the threat landscape changes |
| How? | Actions that can be taken to mitigate each threat |
A messaging service
For our messaging service...
| What? | A way for users to send one another messages... |
| For whom? | ...such that only the sender and intended receipient may read the content... |
| From whom? | ...yet third parties, such as other users, the service provider, and law enforcement may not... |
| Any limitations? | though it may be possible to determine who is sending messages and when. |
| How? | To be continued! |
Artifacts
That slide had too many words.
We can instead proceed in four steps.
- Diagram: What are we building?
- Identify threats: What could go wrong?
- Mitigate:What are we doing to defend against threats?
- Validate: Have we acted on each of the previous steps?
Process
I think of this as a procedural way to go from an idea, to an idea where the threats are modelled.
- First, we draw a diagram of our idea.
- Then we supplement with the risks or threats.
- Then we explain how each is addressed.
- The last stage, validation, is completed after implementing the idea by testing and studying the service.
Signal
"Signal is a cross-platform encrypted instant messaging service... Users can send one-to-one and group messages, which can include files, voice notes, images, and videos."

ABE
- There is a traditional approach.
- Alice is used to denote "user A"
- Bob is used to denote "user B"
- Eve is used to denote an "eavesdropper"
- An aside: What do we think about the choice of these names?
- What if Calvin is used to denote "user C"?

source: xkcd.com/1323
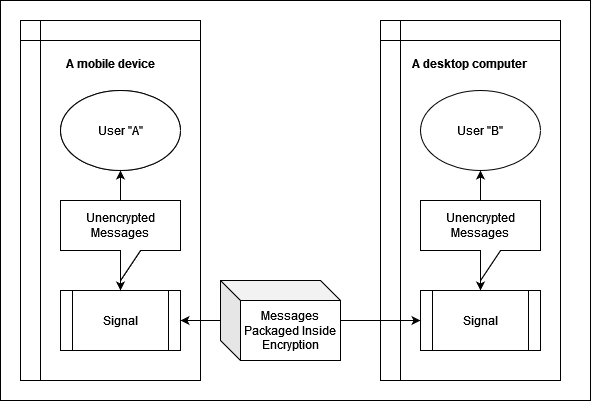
Diagram
Signal is a... instant messaging service.
Diagram
Signal is a... encrypted instant messaging service.
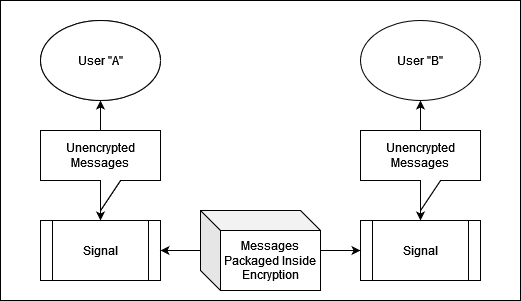
Diagram
Signal is a cross-platform encrypted instant messaging service.
Identify Threats
What could go wrong?
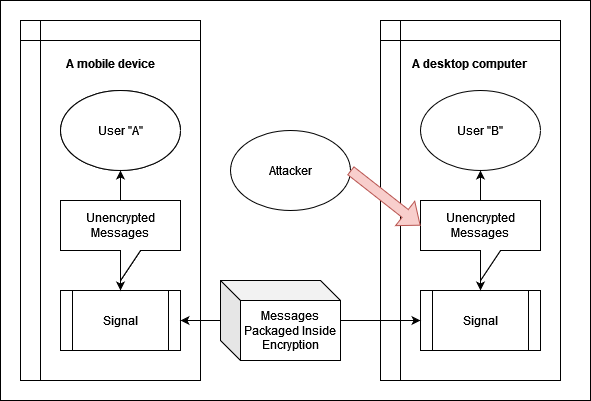
Identify Threats
Some thoughts
- Is the encryption secure?
- Is the device on which unencrypted messages are read/written secure?
- Are messages encrypted on one platform readable on another platform?
- Is encryption too computationally intense to work on a mobile device?
Mitigation and Validation
These things are hard - but we must first ask the right questions.
- Signal is open source, and subject to community scrutiny.
- Signal has been demonstrated and is used by many users.
- Signal is recommended by privacy, technology, and activist communities.
- Is this enough?
Best Practices
Five techniques for success
- Define the scope and depth of analysis.
- Gain a visual understanding of what you’re threat modeling.
- Visually model the attack possibilities.
- Identify threats.
- Document of missing or weak security controls.
Define the Scope
- Determine stakeholders
- Who uses the service?
- Who provides the service?
- Who benefits from the service?
- Who does not benefit from the service?
- Who can answer these questions?
- Are they the same or different people?
- Should you do this by yourself?
- What do you do if you need help?
Visual Understanding
I made this in draw.io

Identify Threats
Who do you not want reading your messages?
Document
There are established norms for secure code - what about other services?
Now consider
A commercial airliner:
- Serves both a crew and passengers.
- Has a flight deck.
- Has a service station which is for both crew and passengers.
- Crew and passengers both must have access to the service station.
- Crew only must have access to the flight deck.
- Passengers must not have access to the flight deck.
Artifacts
We can instead proceed in four steps.
- Diagram: What are we building?
- Identify threats: What could go wrong?
- Mitigate:What are we doing to defend against threats?
- Validate: Have we acted on each of the previous steps?
Model
| Informally | Formally |
|---|---|
| What? | Description of the subject to be modeled |
| For whom? | A way of validating the model and threats, and verification of success of actions taken |
| From whom? | Potential threats to the system |
| Any limitations? | Assumptions that can be checked or challenged in the future as the threat landscape changes |
| How? | Actions that can be taken to mitigate each threat |
Your turn!
A commercial airliner threat model:
- Concerns crew and passengers, a flight deck and a service station.
- Should answer What?, For whom?, From whom?, Any limitations?
- Should include a a diagram and identify threats.
Form groups of 2-4 and create 3-5 slides. [30-45 min]
Homework
Identify something in your life (an app, a work thing, a building, a company) with security features.
- Construct a 3-5 slide threat model including at least one diagram.
- Discuss at least 2 limitations of the existing systems.
- Discuss at a high level how you would address, fully or partially, at least 1 of these limitations.
Be ready to present you slides at 6 PM on 18 Jan!